The ubiquitous presence of mobile devices such as smartphones and tablets, along with the interconnectivity of devices and systems, particularly in the context of the Internet of Things and cloud computing, elevates cyber security to a critical yet often neglected issue within IT organizations. Potential consequences include the loss of competitive corporate secrets, disruption of value creation processes, or significant damage to the organization's reputation, for instance, through the theft of customer data. To protect networks, computer systems, cyber-physical systems, data, and the entire organization from such attacks, vulnerabilities within the entire IT organization must be identified and systematically addressed.
Read More …Start Your Expedition
Operational Excellence
The overarching goal ofOperational Excellence is the continuous optimization of the IT organization in terms of quality, security, speed, and cost. This requires a corporate culture characterized by a constant willingness to change, a high aspiration for quality in all areas, and company-wide transparency.
Specifically, Operational Excellence is about finding the right balance between basic operational tasks and the development of key strategic capabilities. On one hand, day-to-day business must be ensured as efficiently as possible. On the other hand, transformation projects must be carefully managed in terms of time, cost, and risks. Optimally weighing both areas and continuously improving within them often presents challenges for IT organizations.
We support you with our expert knowledge as well as proven methods and models in successfully implementing Operational Excellence in your IT organization.
In Focus
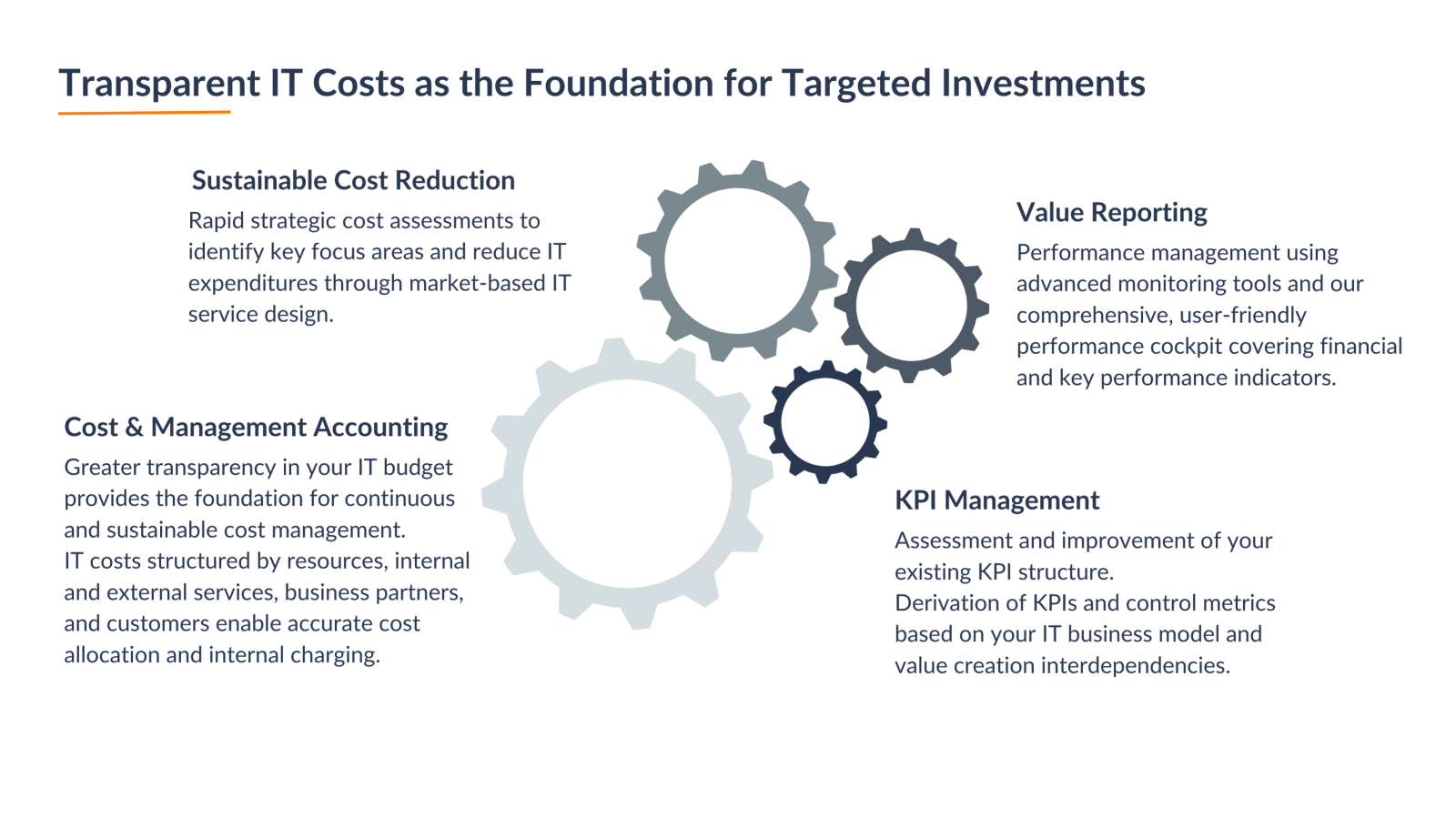
IT Performance Management
Often, IT organizations have evolved historically, making both their system landscape and processes complex and unclear. This directly impacts IT performance. Inefficiencies, unclear responsibilities, dependencies, and a lack of alignment with business needs reduce the effectiveness of the IT organization. IT Performance Management, with a structured approach, identifies processes and competencies that directly influence business outcomes, known as Core IT Services. These services require special focus on their delivery and improvement.
Read More …
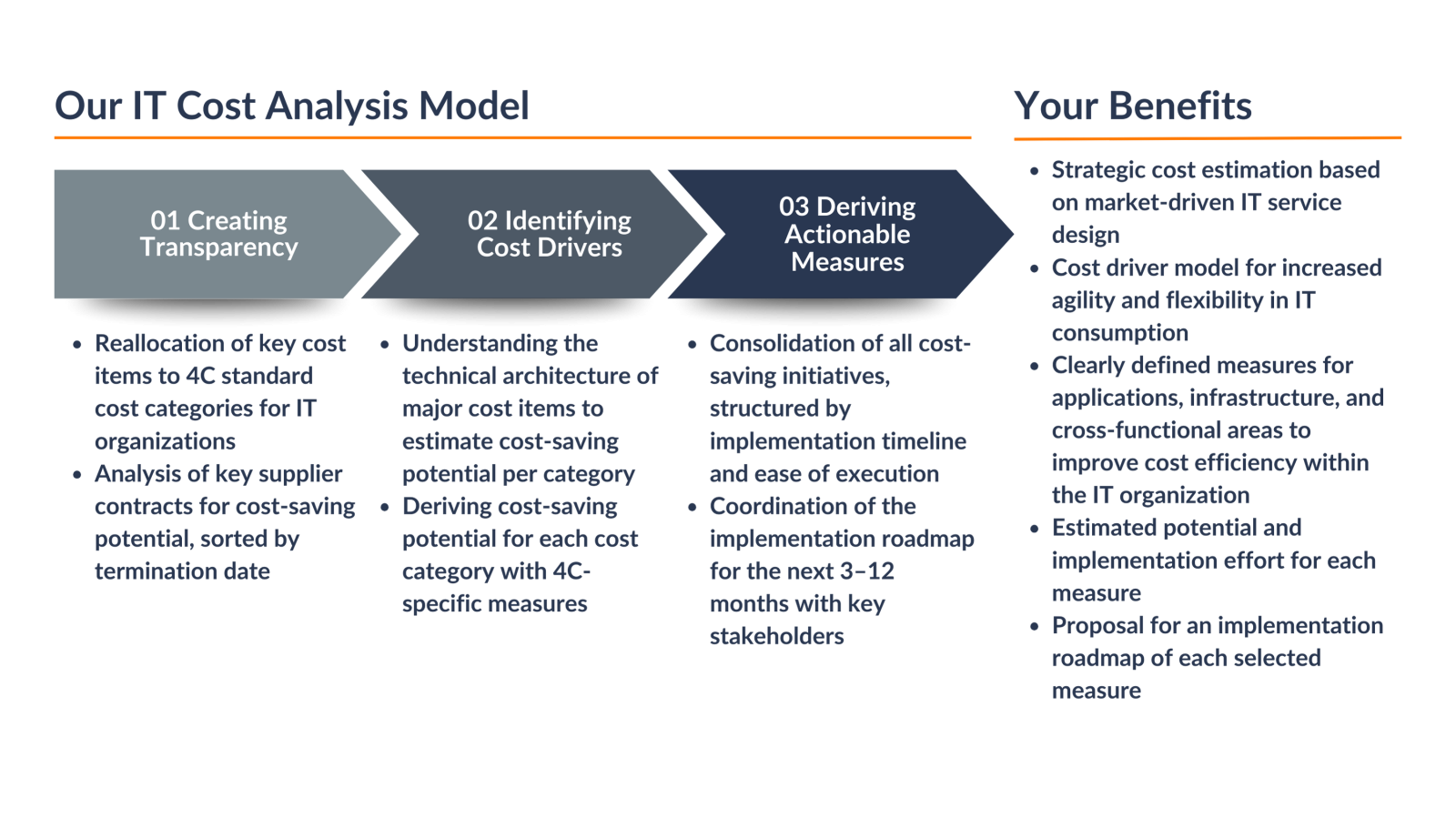
IT Cost Effectiveness
To maintain or even increase innovation in the face of constant cost pressure, many IT organizations must generate their innovation budget independently. However, these organizations often lack transparency in their cost structures and the main cost drivers. Additionally, significant financial resources are tied up in infrastructure and operations (Run activities), leaving little available for forward-thinking projects. Faced with tight IT budgets and the inability to create new positions, we assist CIOs in identifying the right areas to save costs and free up employee capacity. The foundation for this is establishing sustainable cost management with effective control components.
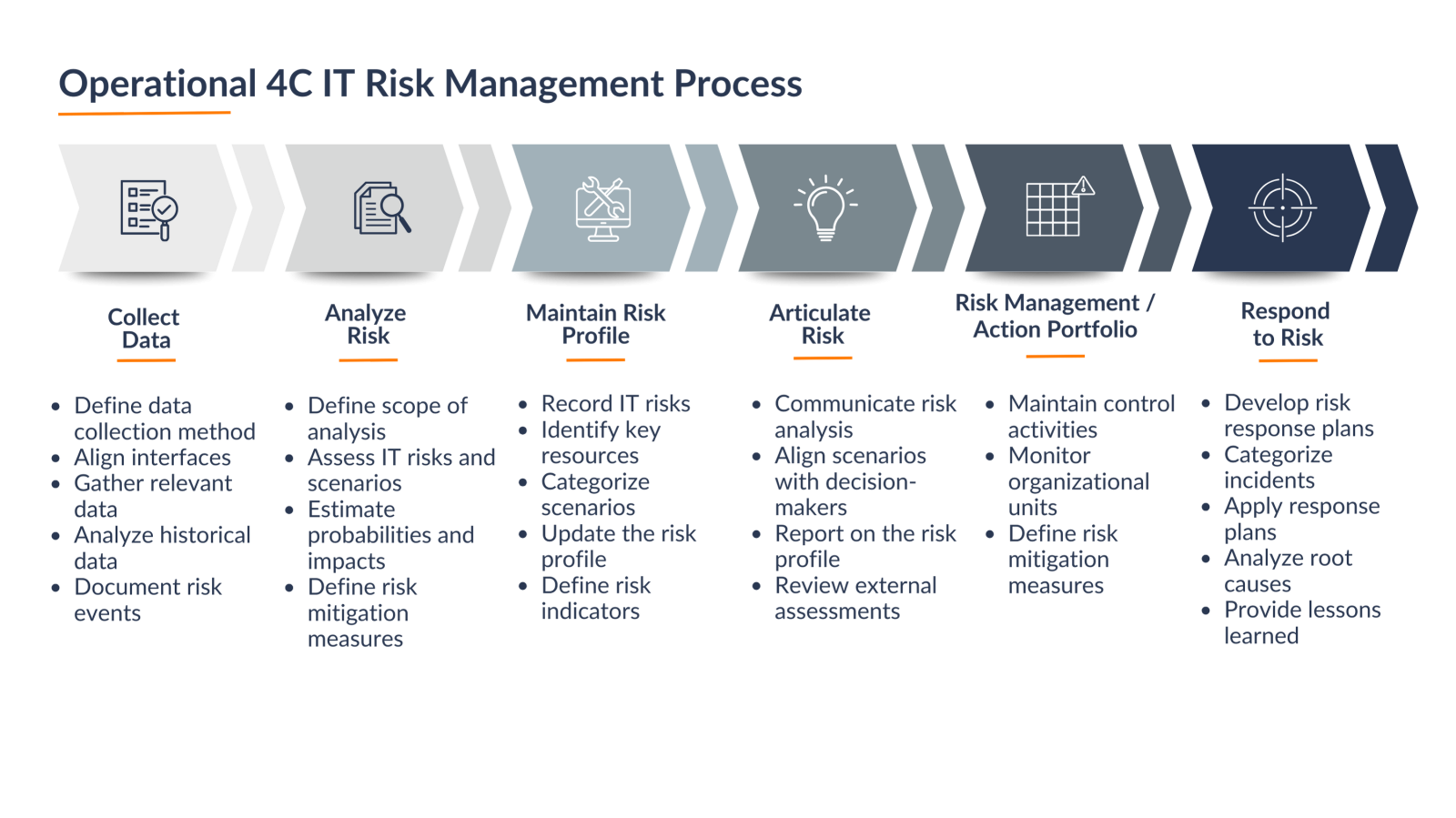
IT Risk Management
IT risk management is an essential component of any IT organization and forms the basis for the secure operation of IT services and functions within a company. From our experience, the challenge in implementing IT risk management often lies in deeply embedding the necessary processes into the entire IT organization. This fundamentally requires considering all relevant interfaces, such as IT governance, the service portfolio, and infrastructure. It has been shown that only a complete integration of the necessary processes into the entire IT organization leads to sustainable success and meets the requirements of certification standards.
Why 4C?
Subject Matter Expertise and Integrated Solution Approaches
Our expertise extends well beyond traditional project management. We offer specific approaches tailored to your needs, combining subject matter expertise, a deep understanding of cultural nuances, and technological know-how. Our teams possess all the necessary disciplines to establish Operational Excellence in your IT organization, including:
- Project Management: We have extensive experience in managing complex transformation projects, often lacking in organizations.
- Technological Expertise: Our profound knowledge of the latest technologies enables us to efficiently transform your ITSM governance model.
- Cultural Awareness: We recognize that the success of implementation also depends on the values and culture of an IT organization. Our teams bring this essential perspective to the CIO domain.
- Customized Transformation Solutions: We offer specific approaches tailored to the unique requirements of your IT organization and the business needs of IT.
Do you have any questions or would you like to find out more about our services?
Contact us for a non-binding consultation.
Insights
4C Study: "Measuring and communicating IT business value"
What is IT Business Value and how can it be measured? What does IT Business Value show and what share does IT have in the company's success?
Publication: "Agilität ist keine Wunderwaffe"
Discover in our publication why agile initiatives fail and how to successfully transform into a flexible IT organization. Learn about delivering customer-centric IT services and the essential roles and structures required.
Article was published in CIO Magazine 2020
4C Study: "Implementation of cybersecurity strategies in the energy sector"
This report provides insights into top management's awareness of cyber risks and highlights security challenges in the supply chain as well as the integration of future technologies.